Repository
Checklist
| Do | Don't |
|---|---|
| ✔️ Have a process to keep dependencies up to date | ❌ Store secrets in source |
Requirements
Project dependencies
Quite often vulnerabilities occur not in our code but in the projects and libraries we use. We can minimise the risk by:
- Using only what you need, don't use dependencies when a single line of code will do
- Use dependencies that you can trust, how many people use it? when was the latest updated? how frequently is it updated?
- Move as many dependencies as possible in out of dependencies and into devDependencies not only will this make bundles smaller but removes unnecessary code from the bundle which might contain vulnerabilities
The good news is that with these dependencies there are many eyes reporting issues and almost as many fixing them. All we need to do is keep our project dependencies up to date.
We can either do this locally via npm and seeing if there are newer versions of packages available and running npm outdated we could then have a look at change logs and choose what version to update to updating the version number package.json and running npm i. Alternatively we can check for vulnerabilities with audit:
# see security issues:
npm audit
# attempt to fix security issues:
npm audit fix
This wont necessarily fix all issues and might end up inadvertently breaking deploys so treat npm audit fix like manually updating npm packages, update and then run tests and see if it deploys. Newer packages doesn't always mean more secure because there are always the risk of new issues, but it does usually mean older security issues have been fixed.
A more automated approach is to set up dependabot on your repo. Only repo owners can access this. Dependabot can inform you of dependency vulnerabilities and even set up automatic PRs to update dependencies.
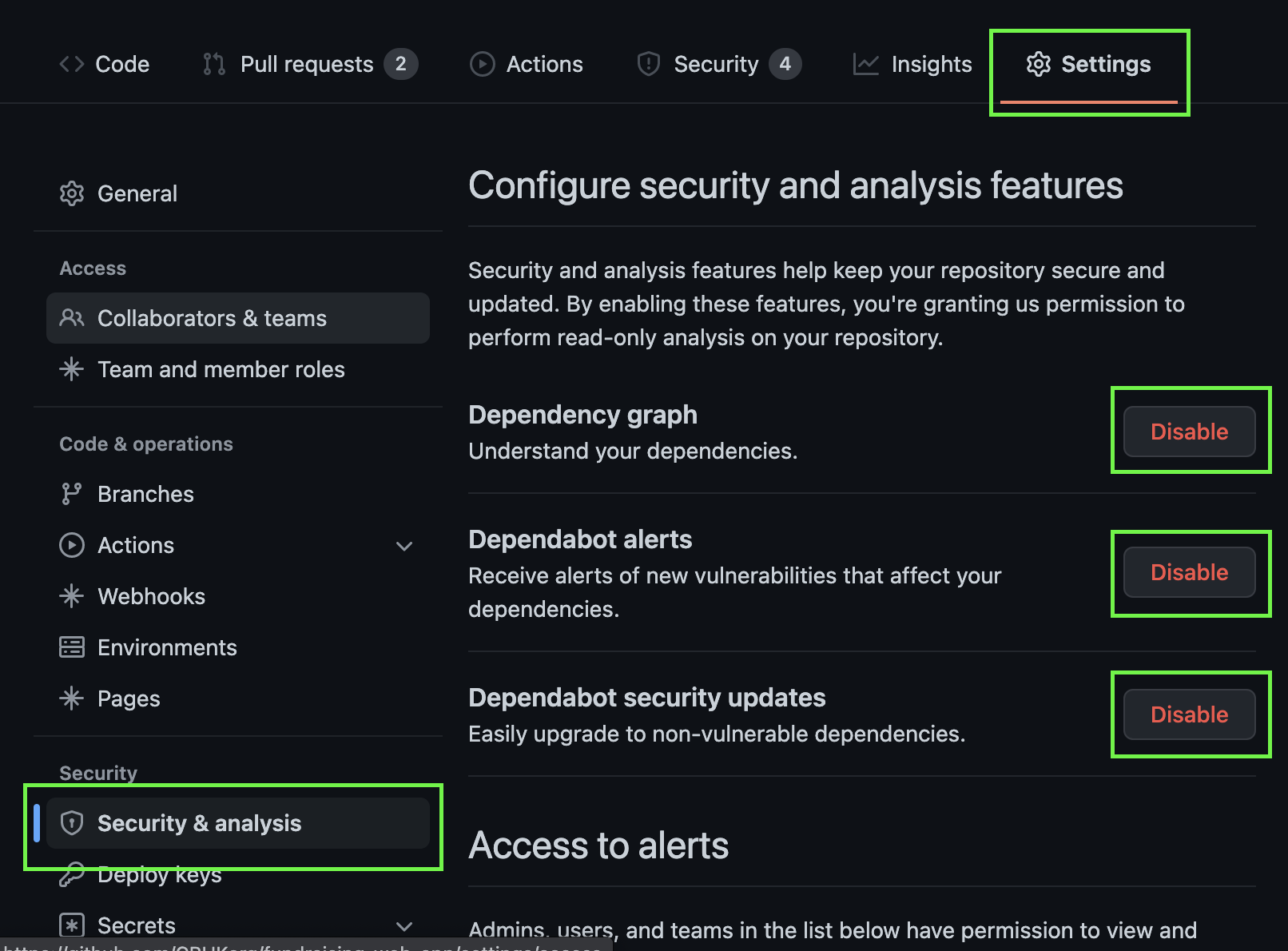
There is also some config for you to add in your repo for example:
.github/dependabot.yml
version: 2
updates:
# GitHub Actions
- package-ecosystem: "github-actions"
directory: "/"
schedule:
interval: "weekly"
day: "monday"
# Npm
- package-ecosystem: "npm"
directory: "/"
schedule:
interval: "weekly"
day: "monday"
# Docker
- package-ecosystem: "docker"
directory: "/"
schedule:
interval: "weekly"
day: "monday"
References & Further Reading
- Github and dependabot config (https://docs.github.com/en/code-security/supply-chain-security)